A Simple Key For AI for customer support Unveiled
A Simple Key For AI for customer support Unveiled
Blog Article
two contributions three several hours back Accomplish harmony in land reclamation projects by conducting EIAs, employing sustainable practices, and interesting regional communities. Civil Engineering Engineering You are drowning while in the chaos of entrepreneurship. How could you remain structured and concentrated?
This looks like a very good attribute, but carrying out checks takes time, resulting in slower general performance. Operating a VPN more than TCP (TCP in excess of TCP) can slow down your link in what’s termed a TCP meltdown.
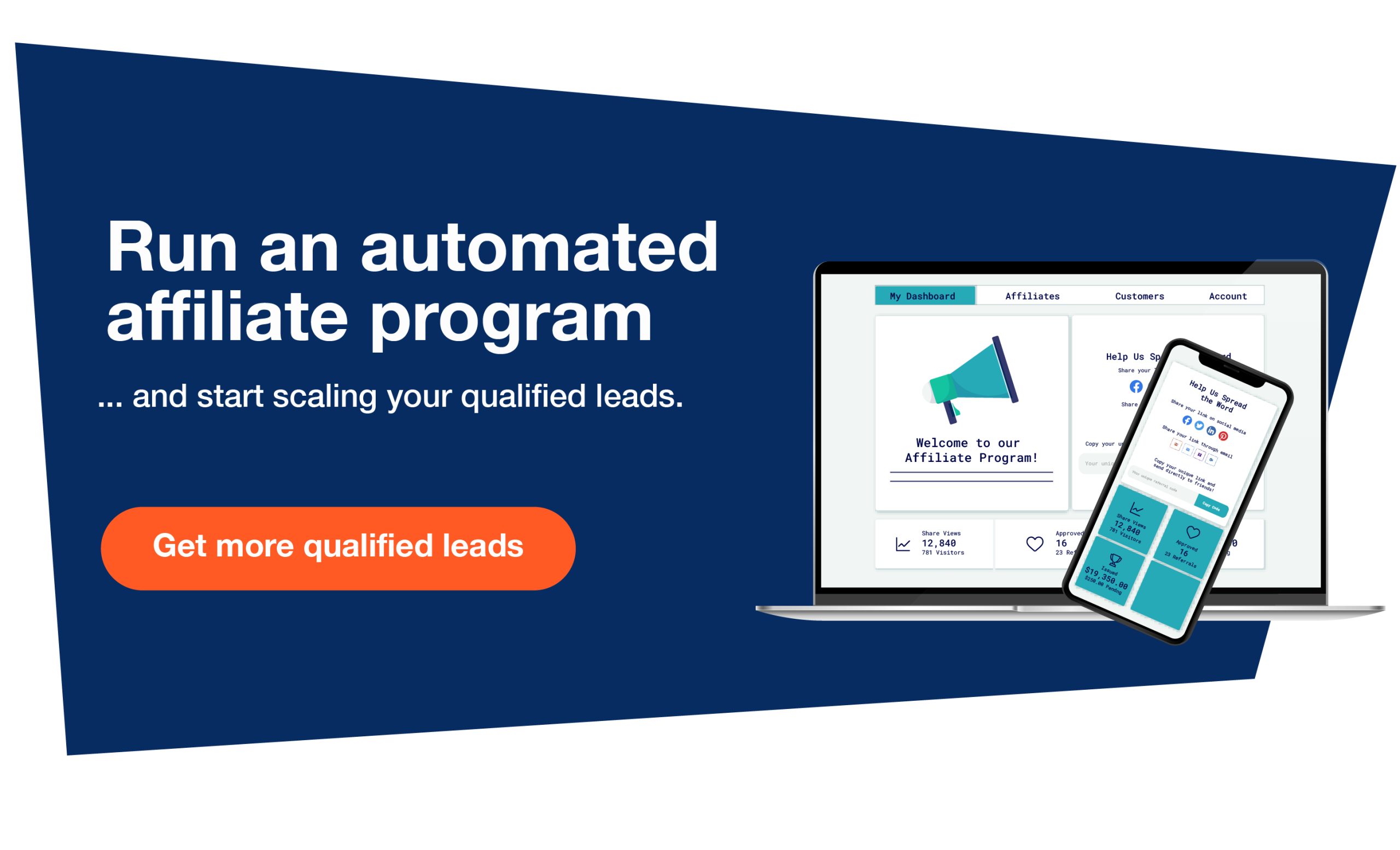
Stephanie from The big apple: Stephanie used to be a housing broker but felt like she was trapped in the grind with no time for herself. Following she located Velocity Profits, she switched over to affiliate marketing and Definitely killed it.
In the event you’ve chosen a customized stealth protocol from a specific VPN company, Then you definately’ll also have to keep your membership Lively to take advantage of it.
Untapped Goldmines: They’re putting you on to site visitors resources that remain Tremendous refreshing. Nobody else is spilling the tea on these, Particularly not for video ads.
4K might be from the menu, but Full HD streaming seems Attractive. Images are ace at 60fps, with no lag or buffering issues. HDR support is a nice contact, boosting colour and distinction for a far more realistic image, while Dolby Atmos will be a welcome bonus for streamers with a home cinema set up.
ExpressVPN: With its Sophisticated obfuscation technological know-how, ExpressVPN is a top choice for end users looking for a reliable and robust Stealth VPN Option. It provides a vast network of large-pace servers across many places throughout the world, guaranteeing seamless access to blocked content and evading VPN detection.
Stealth protocols are used by some VPNs to test to disguise your Internet targeted traffic. This is named “obfuscation”. You'll find other ways To achieve this but the standard approach is to test to encrypt your VPN website traffic once again to remove any ‘metadata’ that could recognize it.
Known vulnerabilities: OpenVPN has no recognised vulnerabilities so long as it is applied with a sufficiently robust encryption algorithm and Perfect Forward Secrecy. It is the marketplace common for VPNs concerned about knowledge security. Firewall ports: OpenVPN could be configured to operate on any UDP or TCP port, like port TCP port website 443, which handles all HTTPS traffic and can make it quite challenging to dam.
Stealth is a new VPN protocol created by Proton. With it, you may entry censored sites and communicate with persons on social networking, regardless if typical VPN protocols are blocked by your government or Firm.
We are able to’t locate the website page you’re seeking. The website page you’re on the lookout for may are already moved, or may possibly now not exist. Try heading again to the prior website page or look at extra content Within this collaborative report site.
Broadway adaptation heading towards the phase with first film's author, movie actor returning to immediate
We started Proton VPN to make sure activists, dissidents, and journalists have secure and personal entry to the online market place. To help keep the Proton community Safe and sound, we only use trustworthy and vetted VPN protocols. The next record displays which VPN protocols are supported in our distinctive applications:
Extended-Expression Wins: You’re not merely trying to find small-time period success below; you’ll learn how to scale your campaigns for ongoing, sustainable income.